Immersive Translate Extension Major Security Vulnerability: Webpage Snapshot Feature Causes Massive User Data Leakage
Recently, the widely acclaimed browser translation extension “Immersive Translate” has been thrust into the spotlight due to a critical security vulnerability. The extension’s webpage snapshot feature has led to massive leakage of user sensitive information to the public network, while a previous controversial decision to restrict third-party APIs has plunged it into both technical and trust crises.
I. Event Core: Security Disaster Caused by Webpage Snapshot Feature
The trigger for the “Immersive Translate” security incident stems from a fatal design flaw in its webpage snapshot feature.
1. Technical Vulnerability Exposure According to feedback from the technical community and users on platforms like Bilibili, the “Immersive Translate” webpage snapshot feature allows users to generate and share HTML files of webpage content. These files are uploaded to Tencent Cloud Object Storage (COS), but the storage server is set to public access without any authentication or permission controls. This means anyone with the link can directly access the files. More seriously, these links may be indexed by search engine crawlers, leading to complete data exposure.
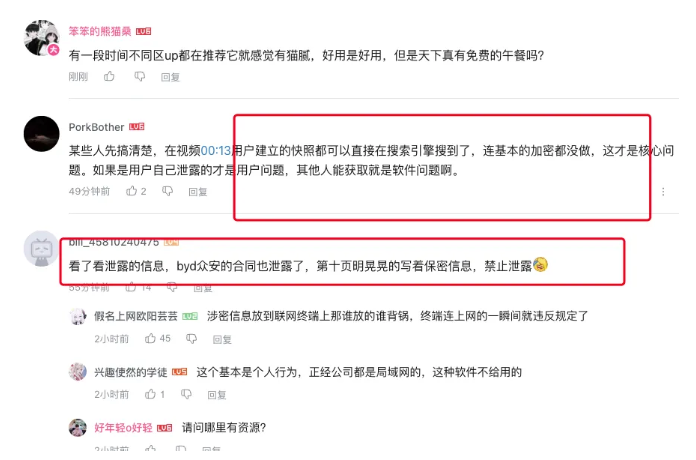
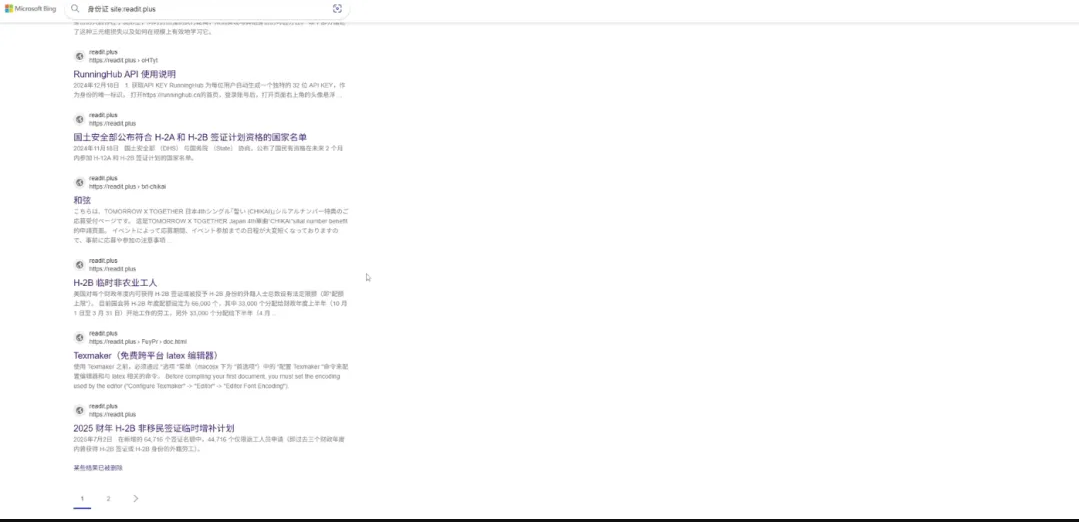
2. Shocking Leaked Data The leaked content covers a wide range of sensitive information, including:
- Personal Privacy: ID card numbers, addresses, personal resumes, etc.
- Business Secrets: Contracts, financial statements, project proposals
- Intellectual Property: Academic papers, research reports
- High-Risk Information: Cryptocurrency mnemonics, API keys, etc.

II. Trigger: Community Backlash Over Third-Party API Restrictions
Before the security vulnerability was exposed, “Immersive Translate” had already sparked strong community dissatisfaction due to a commercialization decision, laying the groundwork for the crisis.
1. Controversial Decision The development team had announced plans to prohibit users from using unauthenticated third-party translation APIs, citing “data security protection” as the reason. However, the extension’s openness—allowing users to freely connect APIs—was one of its core attractions. This move was interpreted by the community as commercially driven, aimed at increasing official API usage by restricting user choices, sparking widespread resistance.
2. Ironic Contrast The reason for restricting APIs was “privacy protection,” but this formed a sharp contrast with the subsequent exposure of massive data leakage. Community trust in the development team was severely damaged, with some users directly pointing out their “inconsistency between words and actions.”
III. Official Response: Apologies Fail to Restore Trust
Facing the public opinion storm, the development team quickly took crisis public relations measures, but with limited effect.
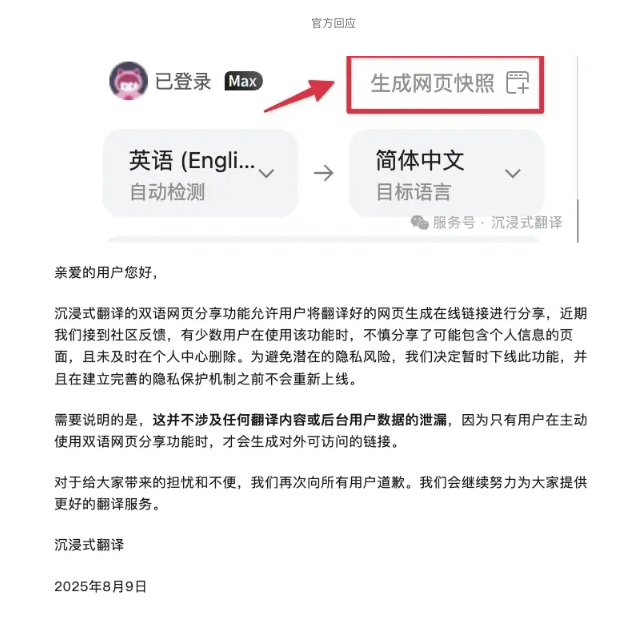
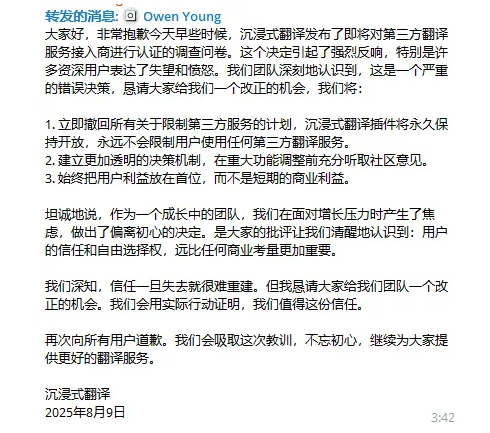
1. Official Response The team issued an apology statement, admitting the API restriction decision was wrong, attributing it to “anxiety under growth pressure,” and promising to revoke related plans and permanently maintain the extension’s openness. However, the statement was criticized for avoiding the main issues:
- The API restriction announcement was downplayed as a “survey questionnaire,” criticized for confusing the public
- Insufficient attention to the technical causes and remedial measures of the data leakage incident, failing to directly address the core problems
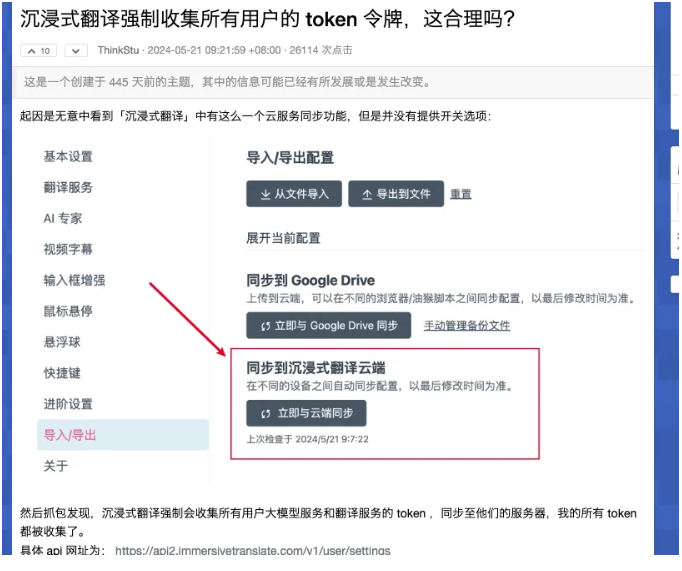
2. Early Warnings Ignored According to information from technical forums like V2EX, long before the incident broke out, developers had already warned about the extension’s irregular behavior in data processing, such as unauthorized uploading of API keys to their own servers. These signals were not given sufficient attention until the vulnerability was fully exposed.
Related Links
More Articles
![OpenAI 12-Day Technical Livestream Highlights Detailed Report [December 2024]](/_astro/openai-12day.C2KzT-7l_1ndTgg.jpg)