Major Security Alert: VS Code's Most Popular Theme Extension Material Theme Found to Contain Malicious Code
Incident Overview
Material Theme, a highly popular VS Code theme extension with over 3.9 million installations, was discovered to contain malicious behavior in its codebase in February 2025, specifically within a dependency named Sanity.io. This dependency, which hadn’t been updated since 2016, may have been compromised, potentially leading to user data leaks. Microsoft swiftly responded by removing the extension from the marketplace on February 25 and banning the publisher Equinusocio. Developer Mattia Astorino later argued that the issue was merely an outdated dependency that could have been easily fixed, but Microsoft provided no notice—a claim that sparked community debate.
Timeline
- February 2025: Security researchers discover and report malicious code
- February 25, 2025: Microsoft confirms issue, removes extension and bans publisher
- February 26, 2025: Public reports and articles begin detailing the incident
- February 27, 2025: Community discussions continue, with some developers attempting to fork the repository to provide secure versions, such as t3dotgg’s fork (vsc-material-but-i-wont-sue-you).
Detailed Report
Introduction
In February 2025, the VS Code Material Theme extension was removed from the marketplace after being found to contain malicious code, sending shockwaves through the developer community. Published by Equinusocio, the extension had amassed 3.9 million installations, affecting a vast user base. This report details the incident timeline, malicious code behavior, stakeholder responses, and implications for software supply chain security.
Background
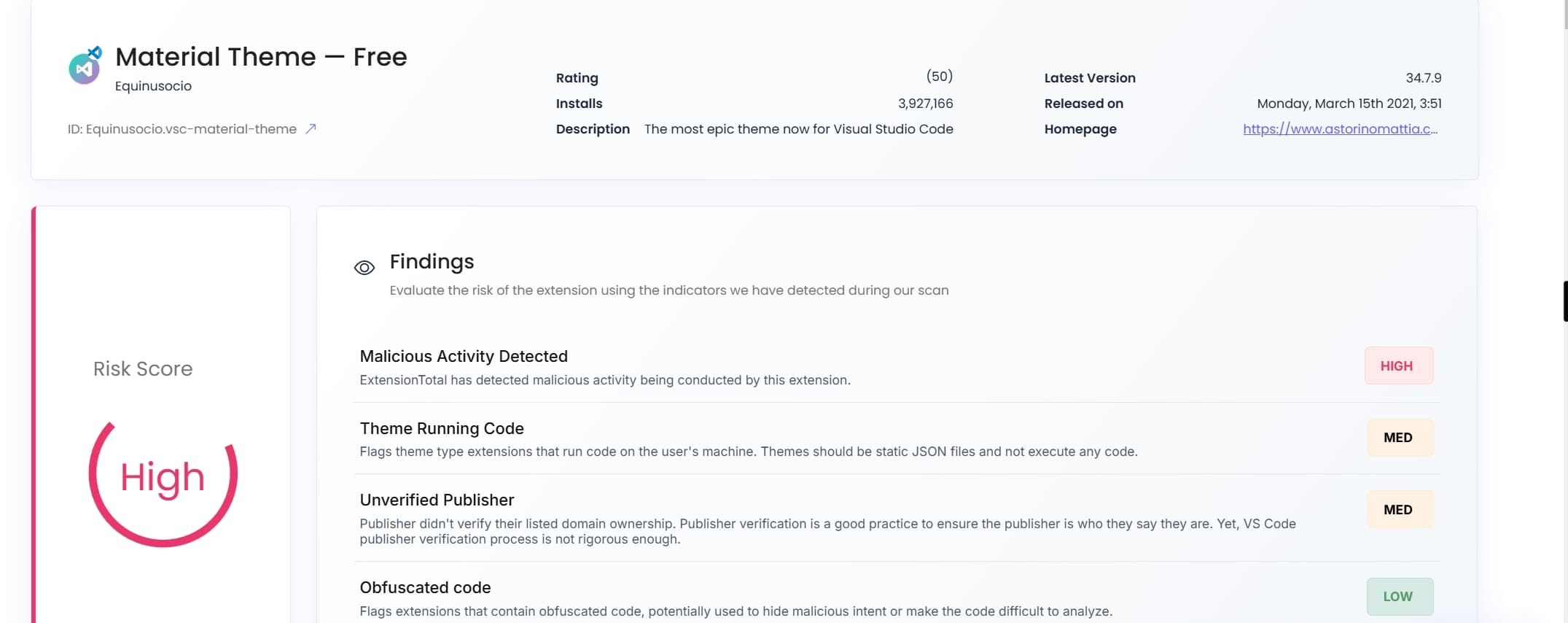
Material Theme is a theme extension for Visual Studio Code (VS Code), developed by Mattia Astorino (known as Equinusocio). The extension offers various customization options and was highly popular among developers. At the time of the incident, it had over 3.9 million installations, with its companion extension “Material Theme Icons — Free” exceeding 5 million installations, totaling 13 million installations.
Discovery and Behavior of Malicious Code
In February 2025, security researchers Amit Assaraf and Itay Kruk discovered multiple suspicious markers in the Material Theme extension’s codebase while conducting security scans of VS Code extensions. They reported their findings to Microsoft, whose security research team subsequently confirmed these allegations and uncovered additional suspicious code.
Summary Details
| Aspect | Details |
|---|---|
| Extension Name | Material Theme — Free |
| Installations | 3,927,094 |
| Malicious Component | Present in compromised Sanity.io dependency |
| Publisher | Equinusocio (real name: Mattia Astorino) |
| Related Extension | Material Theme Icons — Free, over 5 million installations |
| Total Publisher Installations | 13,177,186 |
| Marketplace Action | Removed from VS Code marketplace, Microsoft removed other publisher associations with Mattia Astorino |
| Impact | Exposed approximately 4 million developers and countless organizations |
| Analysis Report Source | extensiontotal.com report |
| Security Advice | Check environment for infection using IOCs or contact extensiontotal.com |
Microsoft’s Response
Microsoft took decisive action after confirming the malicious code:
- Removed Material Theme — Free and Material Theme Icons — Free from the VS Code marketplace on February 25, 2025
- Banned publisher Equinusocio from publishing any extensions on VS Marketplace
- Automatically uninstalled the extension from all VS Code instances running it
Microsoft clarified in a statement that the removal was solely due to potential malicious intent, not copyright or licensing issues Hacker News post.
Developer’s Response
Mattia Astorino issued a statement attempting to explain the situation. He claimed the only issue was an outdated Sanity.io dependency from 2016 used for displaying release notes. He further argued that while the dependency might have been compromised, he could have fixed it in 30 seconds if Microsoft had notified him. However, Microsoft’s direct removal without contact sparked community controversy (source: Bleeping Computer report).
Personal Insights
As a developer, I can’t help but wonder if the developer community needs stronger tools to monitor dependency security. While Astorino’s defense has merit, failing to update dependencies was negligent, and Microsoft’s quick response, though protective of users, may have caught some innocent users off guard. Perhaps a more transparent communication mechanism could be established that both protects users and gives developers a chance to correct issues.
Conclusion
The Material Theme extension incident serves as a cautionary tale about software supply chain security, reminding developers to regularly update dependencies and calling for marketplace operators to strengthen security reviews. The incident continues to evolve, with more details likely to emerge.
Key References
More Articles
![OpenAI 12-Day Technical Livestream Highlights Detailed Report [December 2024]](/_astro/openai-12day.C2KzT-7l_1ndTgg.jpg)