Security Alert: One API Docker Image Suspected Poisoning Attack
Event Timeline
Last Updated: 2024-12-29 20:00 UTC+8
Issue Discovered by:
@luojiyin1987finisitinerisand others, Original Report
Project Maintainer:
@songquanpeng
Incident Overview
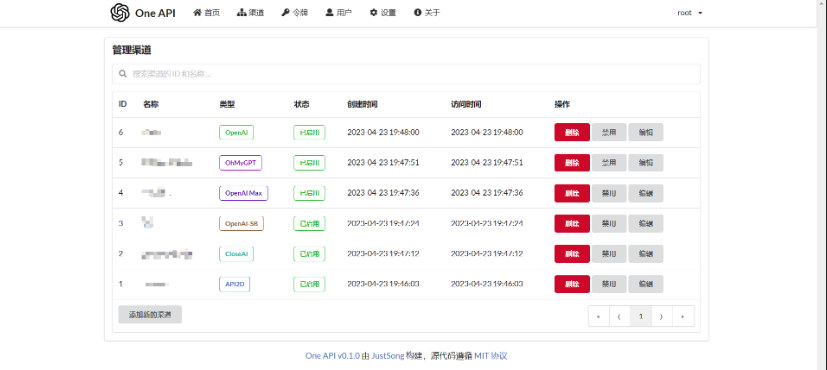
On December 27, 2024, security issues were discovered in the One API project’s Docker Hub images. Attackers obtained the project maintainer’s Docker Hub credentials and pushed malicious image versions (v0.6.5-v0.6.9) containing mining malware. These compromised images caused abnormal CPU usage on affected servers, impacting normal system operations.
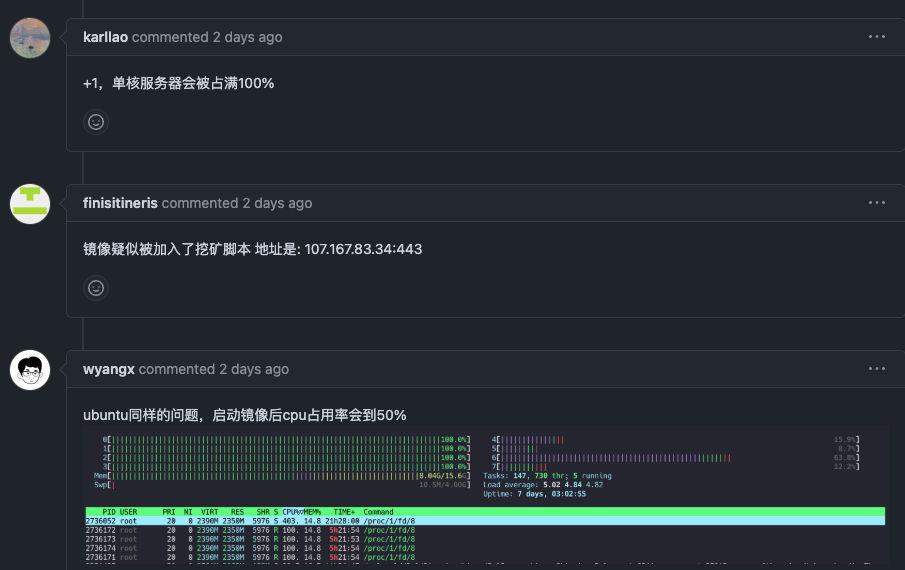
Observed Issues
- Servers running affected versions show approximately 50% CPU usage
- Suspicious network connections to mining pool server (107.167.83.34:443)
- Mining pool addresses pointing to supportxmr.com and c3pool.org
Official Response
Project maintainer @songquanpeng took immediate action:
- Revoked all Docker Hub access tokens
- Reset account password and enabled 2FA
- Temporarily disabled GitHub Actions
- Temporarily removed all project collaborator access
- Planned to push clean image versions
Security Recommendations
For users who have deployed One API, we recommend:
- Immediately check if you’re using affected versions (between v0.6.5-v0.6.9)
- If using affected versions:
- Stop and remove affected containers
- Delete suspicious Docker images
- Restart servers to ensure complete cleanup
- Docker container usage recommendations:
- Add
--cap-drop=ALLparameter to limit container permissions - Regularly check system resource usage
- Use
htopor similar tools to monitor suspicious processes
- Add
Technical Analysis
-
Attack Method:
- Attackers pushed Docker images containing mining software (xmrig)
- Affected images automatically connect to specified mining pools
-
Impact Scope:
- Only affects versions v0.6.5-v0.6.9 updated after December 27, 2024
- Earlier versions and images from other sources (e.g., ghcr.io) are unaffected
-
Security Audit Recommendations:
- Use tools like Lynis for system security audits
- Check for abnormal network connections and processes
Future Recommendations
-
User Level:
- Use officially verified secure image versions
- Regularly update to the latest secure versions
- Implement container security best practices
-
Project Maintenance Level:
- Strengthen CI/CD pipeline security
- Implement stricter image signing verification
- Establish security vulnerability response mechanisms
This incident serves as a reminder to exercise caution when using Docker images. Users should always obtain images from trusted sources and remain vigilant. Project maintainers are advised to enhance security measures to prevent similar incidents.
References
More Articles
![OpenAI 12-Day Technical Livestream Highlights Detailed Report [December 2024]](/_astro/openai-12day.C2KzT-7l_1ndTgg.jpg)